Detect Web3 Frontend Attacks with dAppling DNS Monitor
TL;DR: We built dappling.network/monitor to help prevent web3 DNS hijacking attacks. This tool alerts you to potential DNS hijacking. By monitoring over 3,000 Web3 domains (everything on DeFiLlama) for nameserver changes, it helps you be aware when domains are hijacked. Try the tool now and be part of a safer DeFi community.
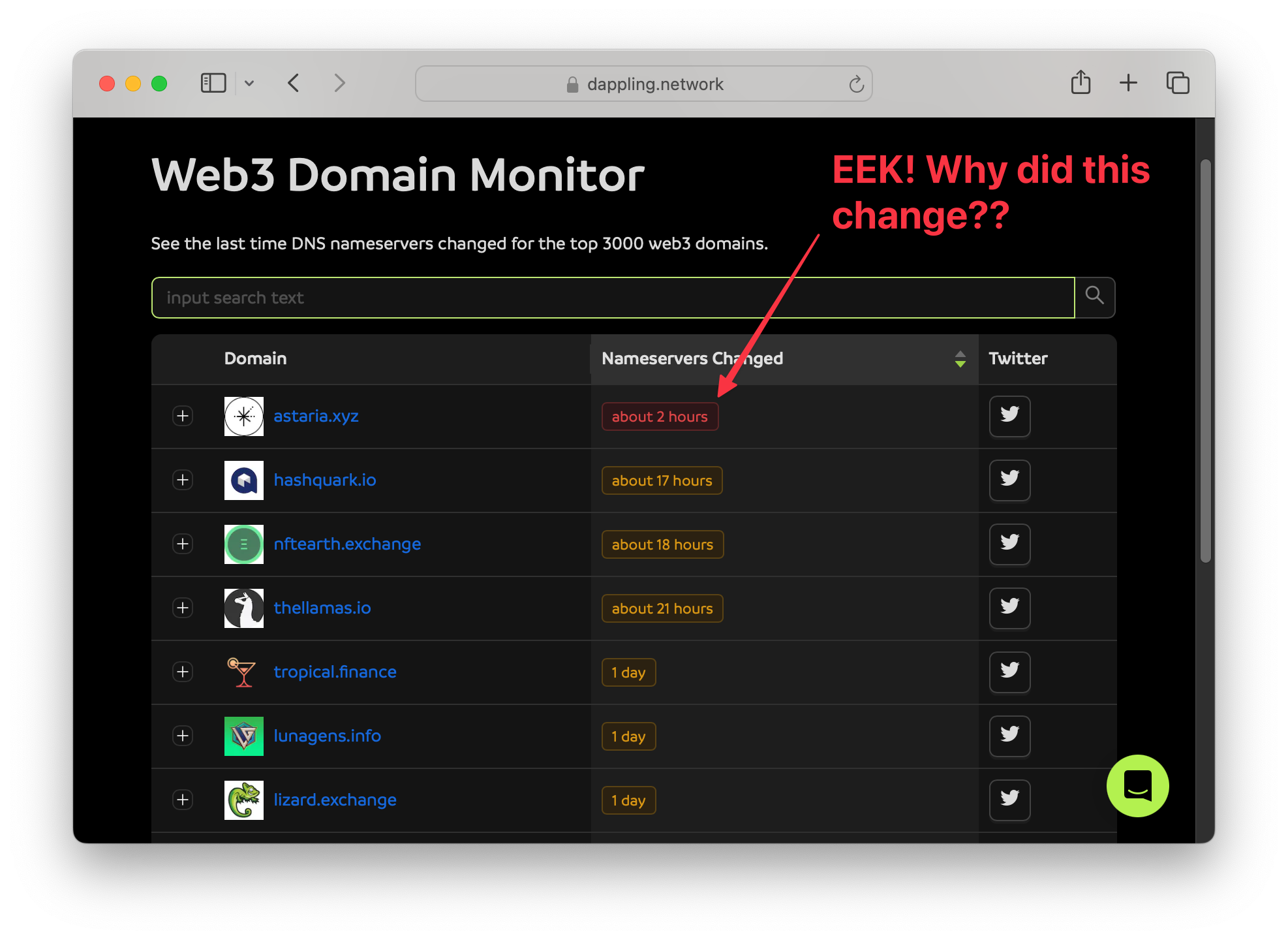
Why is this needed?
In the last few months there have been several DNS hijacking attacks targeting web3 protocols. These included Frax, Balancer, Galxe, Velodrome, and Aerodrome to name a few.
They all happened the exact same way. The DNS registrar they were using was social engineered, and the hacker was able to change the nameservers and take control over the domain.
These nameserver changes is exactly what the tool looks for and would have detected all 5 of those attacks.
How it works?
We used DeFiLlama to build our original lists of sites to monitor. We then use cloudflare’s DNS over HTTPS api to check each of the nameservers for changes every 5 minutes. If we detect a change, we send out a notification to everyone who subscribed to nameserver changes for that domain + update the monitoring table.
We also automatically add all dappling.network production domains to the monitor list + they get extra features to help them protect their users against these types of attacks.
Next Steps
- Check out the tool + signup for notifications for your most used site
- Deploy your site on dAppling to get this + other security features with 0 config.
- DM me on twitter if you have questions or want a site that’s missing added.
Video Demo
Thank you
Thank you to the dAppling team for building the tool. CerealSabre from eth.limo for helping me brainstorm this idea and Derrick from Lume for helping me understand DNS at a deeper level. Also huge shout out to the 3DNS team who’s helping reduce the DNS hijacking problem with their hybrid domains.
